Data‑Sharing Agreements for Visa Partners: Legal Clauses You Shouldn’t Skip

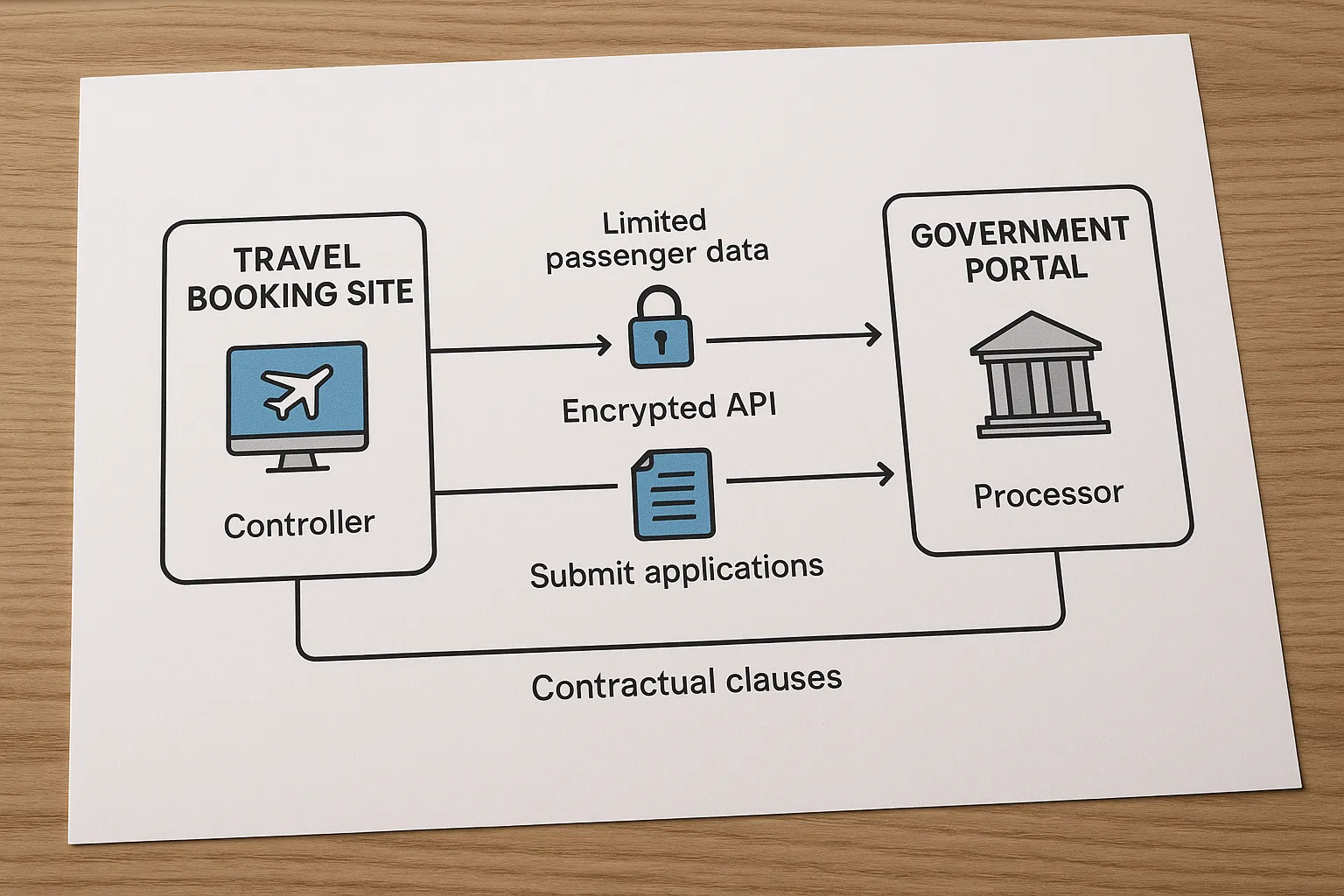
International visa processing has become a data-intensive, API-driven business. Whenever an airline, OTA, cruise line or tour operator integrates an eVisa provider like SimpleVisa, personal data flows back and forth in milliseconds—passenger names, passport scans, payment tokens, even biometric hashes. All of that exchange must sit on rock-solid legal footing. Enter the data-sharing agreement (DSA).
Yet too many travel brands still copy-paste generic NDAs or rely on boilerplate “data processing addenda” that gloss over critical obligations. Regulators won’t be so forgiving in 2025: GDPR fines have already topped €4 billion, and new laws such as the EU Data Act and U.S. state privacy statutes keep raising the bar.
This guide walks you through the essential clauses you cannot afford to skip when drafting or reviewing a DSA with a visa-management partner.

Why a Robust Data-Sharing Agreement Matters
- Regulatory compliance: GDPR, UK GDPR, CCPA/CPRA, PIPEDA, PDPA, and sector-specific rules (e.g., IATA Resolution 792 on personal data) all require clear allocation of controller/processor roles and technical safeguards.
- Brand trust: A single data breach can wipe out customer confidence and fuel abandonment of ancillary services—including eVisa upsells your revenue team depends on.
- Operational clarity: Well-defined data flows, retention limits, and service-level targets minimise disputes between product, engineering and legal teams post-go-live.
10 Legal Clauses You Shouldn’t Skip
| # | Clause | Risk Mitigated | Sample Language Snippet |
|---|---|---|---|
| 1 | Purpose & Scope | Function creep; unlawful processing | “Visa Partner shall process Shared Data solely for assessing visa eligibility, submitting applications, and providing status updates related to Booking ID.” |
| 2 | Data Categories & Minimisation | Over-collection; excess liability | “Parties will share only the data fields listed in Annex A (max. MRZ, photo, itinerary). Any additional fields require written consent.” |
| 3 | Lawful Basis & Consents | GDPR Art. 6 violations; fines | “Travel Merchant acts as Data Controller and warrants a valid Art. 6(1)(b) contractual basis; Visa Partner acts as Processor.” |
| 4 | Security & Encryption Standards | Breaches; ransomware | “Visa Partner shall maintain ISO 27001 certification and encrypt data in transit (TLS 1.3) and at rest (AES-256).” |
| 5 | Sub-processing & Onward Transfers | Shadow vendors; Schrems II issues | “No sub-processor may be engaged without 30 days’ notice and equivalent SCCs/UK IDTA in place.” |
| 6 | Breach Notification & Incident Response | Regulatory reporting gaps; delayed comms | “Processor will notify Controller within 24 hours of discovery, provide a mitigation plan within 48 hours, and cooperate on DPA filings.” |
| 7 | Data Subject Rights Assistance | SAR backlogs; fines | “Processor shall, within 72 hours, support Controller in fulfilling access, erasure, portability, or restriction requests.” |
| 8 | Retention & Deletion | Excess storage costs; audit exposure | “Shared Data shall be deleted or irreversibly anonymised 90 days after visa expiry unless longer retention is required by law.” |
| 9 | Audit & Compliance Reporting | Undetected non-compliance | “Controller may conduct one annual security audit (remote or on-site) with 15 days’ notice; Processor will provide SOC 2 Type II report.” |
| 10 | Liability, Indemnification & Insurance | Uncapped exposure | “Each Party’s aggregate liability is capped at 125% of fees paid in the preceding 12 months, except for wilful misconduct or GDPR fines caused by breach.” |
1. Purpose & Scope
Tie data use directly to the passenger’s visa transaction. This avoids “scope creep” where marketing teams reuse sensitive data for unrelated campaigns—an instant GDPR red flag.
2. Data Categories & Minimisation
List every field explicitly. Doing so forces teams to rationalise whether they really need to pass, for example, a full travel history when a single passport number suffices.
3. Lawful Basis & Consents
Under GDPR, you must state who is controller and who is processor. Most travel sellers remain the controller because they decide why data is processed; visa providers act as processors carrying out instructions.
4. Security & Encryption Standards
Merely stating “industry-standard security” no longer cuts it. Reference concrete frameworks—ISO 27001, SOC 2, NIST SP 800-53—and minimum encryption levels. For API traffic, insist on TLS 1.3 with HSTS.
(For deeper technical guidance, see our internal post Top 8 Security Features to Demand in Any Electronic Visa Solution.)
5. Sub-processing & Onward Transfers
Visa providers often rely on cloud infrastructure (AWS, GCP) or payment gateways. Make sure your DSA forces them to flow down identical privacy obligations—and to notify you before any new sub-processor is added.
6. Breach Notification & Incident Response
GDPR requires reporting a breach to regulators within 72 hours after becoming aware. Contractual 24-hour notice from your partner gives you a buffer to investigate and draft the supervisory-authority report.
7. Data Subject Rights (DSRs)
When a traveller requests deletion, your ops team cannot chase multiple vendors manually. Binding your visa partner to a 72-hour DSR support window keeps you compliant and your customers happy.
8. Retention & Deletion
Unnecessary data hoarding increases attack surfaces and storage bills. Attach automated deletion schedules to application-status webhooks so both parties purge data in sync.
9. Audit & Compliance Reporting
Reserve the right to audit, but avoid operational disruption by accepting reputable third-party reports (SOC 2 Type II, ISO surveillance audit, penetration-test summaries).
###10. Liability, Indemnity & Insurance
Cap liability but carve out exceptions for gross negligence and non-compliance that results in regulatory fines. Request proof of cyber-liability insurance—many policies now exclude GDPR fines unless explicitly added.
Negotiation Tips & Common Pitfalls
- Align legal with engineering early. Lawyers sometimes promise deletion timelines that devs cannot implement. Parallel-track the contract with an architecture review.
- Watch for silent “legitimate interest” language that lets the processor reuse data for analytics or AI training. Delete or narrow it.
- Scrutinise hosting geography. If your passenger data originates in the EU, be wary of storage in jurisdictions without adequacy decisions unless SCCs plus transfer impact assessments (TIAs) are in place.
- Insist on key-rotation SLAs. Static API keys sitting in a code repo undermine every other security clause. (See Developer Q&A: Best Practices for Authenticating Against the SimpleVisa API.)
- Plan sun-set clauses. If you switch providers, require certified deletion and data portability in a machine-readable format (JSON, CSV) within 30 days.
Pre-Signature Checklist for Travel Brands
- Roles (Controller vs Processor) clearly defined
- Data fields enumerated in an annex
- ISO 27001/SOC 2 evidence received
- Sub-processor list reviewed and approved
- Breach-notification window ≤ 24 hours
- DSR support timeline ≤ 72 hours
- Retention period explicitly stated
- Audit rights and frequency agreed
- Liability cap and insurance certificates attached
- Data-export clause for contract termination
How SimpleVisa Makes Compliance Easier
SimpleVisa was built API-first with privacy by design. Out of the box we provide:
- ISO 27001-certified infrastructure and SOC 2 Type II report
- End-to-end AES-256/TLS 1.3 encryption and signed webhooks
- Configurable data-retention policies (30–365 days)
- Real-time breach-alert channels and 24×7 incident response
- Self-service Data Subject Request portal for partners
Our legal team maintains processor-to-processor SCCs with every sub-vendor and updates clients 30 days before any change—no surprises.
(If you run a no-code widget integration, the same standards apply—see How to Offer White-Label Visa Services Without Writing Code.)
Frequently Asked Questions
What’s the difference between a Data-Sharing Agreement and a Data Processing Agreement? A DPA is required when one party is a processor acting on behalf of a controller under GDPR. A DSA can be broader, governing controller-to-controller sharing or cross-border transfers. Many travel companies embed a DPA as an annex to a wider DSA.
Do I need Standard Contractual Clauses if both companies are in the U.S.? Under GDPR, SCCs are needed only when personal data leaves the European Economic Area to a country without an adequacy decision. If EU resident data is not involved, SCCs are optional—but you may still add them for future-proofing.
How often should we audit our visa partner? Industry best practice is annually, or after any major security incident or material change in processing. Accepting an external SOC 2 report can reduce on-site audits.
Turn Compliance Into Confidence (and Revenue)
A meticulous data-sharing agreement is more than legal hygiene—it’s a competitive edge. When travellers trust you with their passport details, conversion rates climb and ancillary revenue follows.
Ready to integrate visa processing that meets the strictest global privacy standards? Book a 30-minute SimpleVisa demo today and see how our API or white-label app can launch in weeks—with a DSA template your legal team will actually like.