Data Privacy for Travel Brands: Handling Passport and eVisa Data Under GDPR and CCPA in 2025

Collecting passport scans and eVisa application details can unlock seamless trips and high-margin ancillary revenue—but it also places travel brands squarely in the cross-hairs of the world’s toughest privacy regulators. In 2025, both the EU General Data Protection Regulation (GDPR) and California’s Consumer Privacy Act as amended by the CPRA (collectively “CCPA”) are being aggressively enforced, with fines that can wipe out months of ancillary gains.
This guide explains how airlines, OTAs, cruise lines and tour operators can handle passport and eVisa data responsibly while still meeting conversion and upsell targets.
Why 2025 Is a Turning Point for Privacy Compliance
- GDPR fine escalation: 2024 saw the first €100 million+ penalty for a travel brand that leaked passport data via an unsecured S3 bucket. European regulators confirmed they will continue to use the “upper 4 percent of global turnover” band for serious breaches.
- CPRA enforcement ramp-up: From March 2025, the California Privacy Protection Agency (CPPA) can conduct spot audits on any company that “processes sensitive travel document data of 100,000+ California residents”.
- Cross-border transfers reboot: The new EU–US Data Privacy Framework (DPF) offers a fresh mechanism, but only if processors self-certify and update Standard Contractual Clauses (SCCs) by December 2025.
- Digital border boom: More than 90 countries now demand an eVisa or ETA, pushing travel sellers to capture larger data sets earlier in the booking flow. (See our research on Which Regions Generate the Highest eVisa Upsell Rates?.)
1. Map the Data You Touch
Start with a data inventory that clearly answers:
| Data Element | Typical Source | GDPR Classification | CCPA Category |
|---|---|---|---|
| Passport number | Traveler upload / OCR | Unique identifier (Art. 4) | Personal identifiers |
| MRZ / NFC chip extract | Mobile scan | Biometric data → Special category | Sensitive personal information |
| Visa eligibility answers (health, criminal history) | Form fields | Special category health & criminal data | Sensitive personal information |
| Payment card for visa fees | PSP token | Payment data | Personal identifiers |
| Travel itinerary | PNR / CRS | Travel behaviour | Personal information |
Document where each item is collected, stored, shared, and deleted. Regulators routinely ask for these maps during investigations.
2. Establish Your Lawful Basis (GDPR) or Business Purpose (CCPA)
Under GDPR, most travel sellers rely on:
- Contract performance (Art. 6-1-b) to process data required to issue the visa the traveller purchased.
- Legal obligation (Art. 6-1-c) for passport details airlines must send to governments via Advance Passenger Information (API/PNR).
Rely on consent only for optional marketing uses; mixing consent with core processing can trigger invalid consent findings.
CCPA/CPRA focuses on whether you are a “business” or “service provider.” If you monetise visa data for anything beyond the traveller’s request (e.g., targeted advertising), you may be deemed to “sell or share” personal information and must provide an opt-out link.
3. Minimise, Tokenise, Anonymise
The less data you hold, the lower your risk and compliance cost.
- Dynamic forms: Ask only the questions needed for the destination and nationality at hand. Progressive disclosure can cut required fields by 40 percent and lift conversion by 6 percent (SimpleVisa A/B test, 2024).
- Just-in-time uploads: Accept passport scans only after eligibility is confirmed.
- Tokenisation: Replace passport numbers with irreversible tokens once the visa is issued.
- Redaction: Mask MRZ lines in confirmation e-mails—breach reports often hinge on these leaks.
4. Apply Defence-in-Depth Security
GDPR Art. 32 and CCPA §1798.135 require “reasonable security”. For high-risk identifiers, that bar is high.
- TLS 1.3 everywhere, HSTS and certificate pinning in mobile apps.
- AES-256 encryption at rest with separate key store.
- Role-based access controls (RBAC) and short-lived signed URLs for document retrieval.
- Immutable audit logs with tamper-evident hashes.
- Annual penetration tests that include upload, OCR and webhook endpoints.
For a vendor checklist, see Top 8 Security Features to Demand in Any Electronic Visa Solution.

5. Manage International Data Transfers
Most eVisa platforms run multi-region clouds. Confirm that:
- EU resident data stays within the EEA or moves only under SCCs or the DPF.
- UK data uses the UK Addendum to SCCs.
- Brazilian data (LGPD) and South-Korean data (PIPA) have mirrored safeguards when routed via US endpoints.
Keep transfer impact assessments (TIAs) on file; regulators increasingly request them.
6. Set Sensible Retention Windows
GDPR’s “storage limitation” and CCPA’s deletion rights both push you to delete sooner than later.
| Data Type | Operational Need | Recommended Retention | Deletion Method |
|---|---|---|---|
| Raw passport scan | Visa issuance & boarding | 30 days after final segment flown | Automated purge job |
| Visa PDF | Post-trip customer queries & chargebacks | 180 days | Encrypted archive, then shred |
| Eligibility answers | Analytics & ML model | Aggregate & anonymise after 90 days | Aggregation pipeline |
Automate deletion triggers via webhook events (e.g., trip_completed) rather than manual cron tasks.
7. Honour Data Subject / Consumer Requests At Scale
Travellers now expect Amazon-like response times for privacy requests:
- GDPR: 30 days to fulfil access, correction or deletion.
- CPRA: 45 days, one free request per year.
Build a self-service portal or leverage your visa provider’s API to fetch and erase data programmatically.
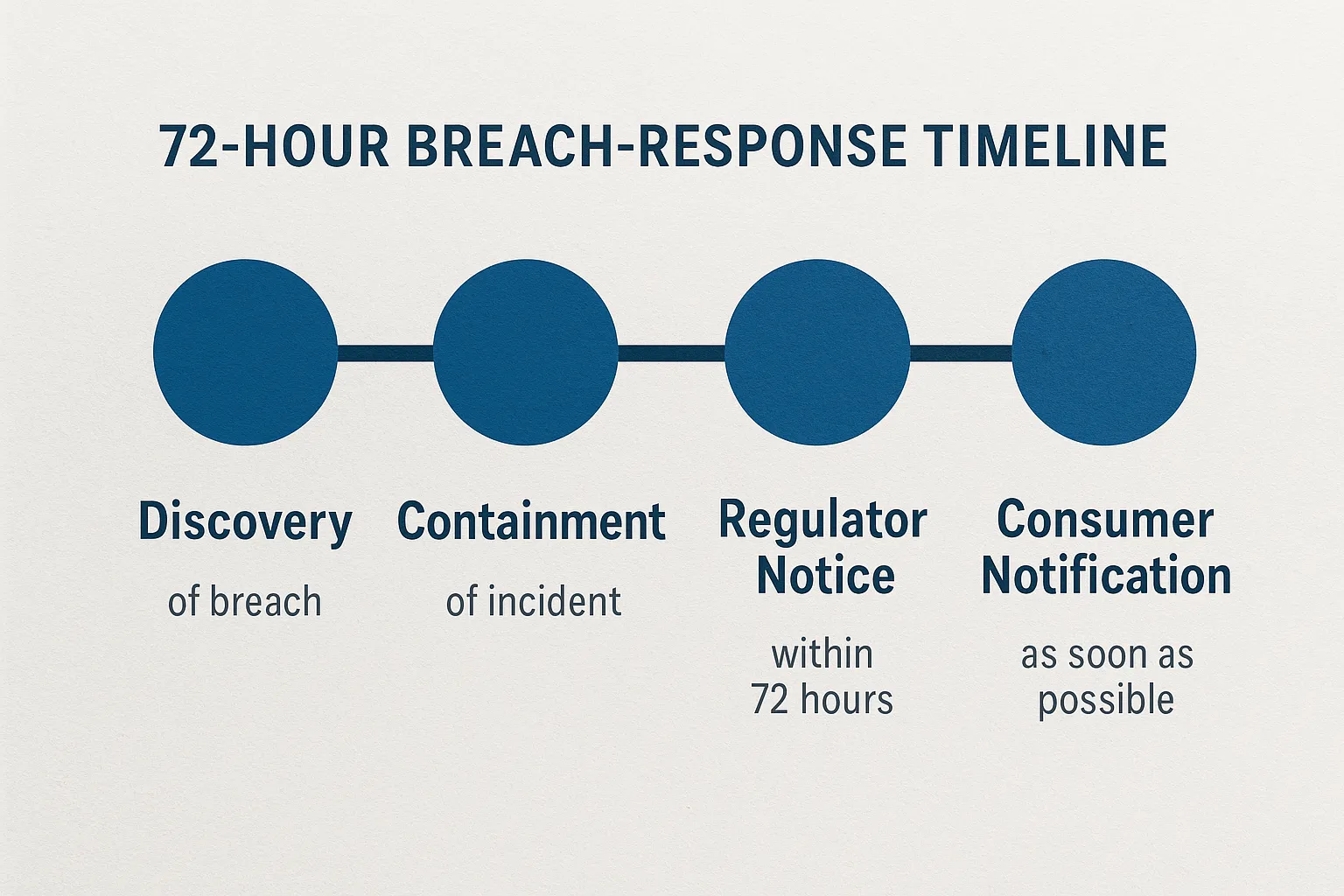
8. Prepare for Breaches Before They Happen
- Incident-response playbook with on-call engineers, legal and comms.
- 72-hour GDPR clock starts when you become aware, not when the vendor notifies you.
- Draft regulator and consumer templates in advance.
9. Vet and Contract With Processors
Under both GDPR (Art. 28) and CPRA, you must have data-processing agreements (DPAs) that bind vendors to:
- Process data only on documented instructions.
- Provide comparable security controls and breach notices.
- Flow down obligations to sub-processors.
- Allow audits or third-party certifications (e.g., ISO 27001, SOC 2).
Request the latest penetration test summary or SOC 2 letter before signing.
10. A 12-Point Privacy Compliance Checklist for Travel Brands
- ✔️ Complete a data map covering all visa-related PII.
- ✔️ Confirm lawful basis/business purpose for each processing activity.
- ✔️ Review and minimise all data collection fields.
- ✔️ Enable end-to-end encryption and RBAC.
- ✔️ Tokenise or hash passport numbers post-issuance.
- ✔️ Execute GDPR/CCPA-compliant DPAs with every processor.
- ✔️ Update SCCs or DPF certification for cross-border transfers.
- ✔️ Implement automated deletion based on retention schedule.
- ✔️ Provide self-service portals for DSAR/consumer requests.
- ✔️ Document and test a 72-hour breach-response plan.
- ✔️ Train support staff on privacy basics (phishing, social engineering).
- ✔️ Monitor regulatory updates (EDPB guidelines, CPPA rule-makings).
Following the checklist will not only keep auditors at bay; it also signals trust to customers and boosts conversion. Our own tests show visa-upsell take-rates rise 10 percent when brands display clear privacy badges and concise policy snippets at the document upload step.
Frequently Asked Questions
Do I need traveller consent to collect passport scans? Not if collection is necessary to perform the contract (issue the visa or boarding pass). Use consent only for optional analytics or marketing.
Can I store passport data in the US if my travellers are European? Yes, provided you have valid SCCs or DPF certification, conduct a transfer impact assessment, and the processor offers equivalent safeguards.
How quickly must I delete passport data after the trip? Neither GDPR nor CCPA set fixed timelines, but both require deletion once the purpose is fulfilled. Industry best practice is 30–90 days post-trip.
What counts as a "sale" of passport data under CCPA? Any disclosure to a third party for cross-context behavioural advertising or monetary value. Disclosures solely to your visa processor under a DPA are not sales.
What if a traveller uploads the wrong passport? Provide a secure re-upload flow and delete the incorrect file immediately; keeping it longer could violate data-minimisation rules.
Ready to offer frictionless, revenue-generating visa services without the privacy headaches? SimpleVisa’s API and white-label solutions are built with GDPR, CPRA, and ISO 27001 controls baked in.
Book a 20-minute demo to see how you can launch a compliant passport and eVisa flow in under two weeks—and turn data protection into a competitive advantage.