Idempotency, Retries, and Webhooks: Reliable Travel API Patterns for eVisa Workflows

Modern travel shoppers expect a single, friction-free checkout. If your eVisa workflow stalls because of a transient network blip, that seat sale or hotel booking can vanish in seconds. According to the 2024 Postman State of the API report, 94 percent of teams rank reliability as the first-or-second most important API quality metric. Yet retries and out-of-order webhooks still catch many travel engineers off guard.
This deep-dive explains three battle-tested patterns—idempotency, retry logic and webhooks—and shows how to combine them for bulletproof eVisa integrations, whether you call the SimpleVisa API directly or another document-automation provider.
Why reliability matters in eVisa flows
- Monetary impact – Duplicate application fees or missing refunds quickly erode ancillary revenue and trigger costly chargebacks.
- Regulatory risk – A lost status update can lead to denied boarding fines or stranded passengers.
- Customer experience – Travelers who have to re-enter a 10-page visa form rarely return.
Because eVisa processing mixes synchronous calls (eligibility look-ups, payment authorisation) with long-running, asynchronous steps (government adjudication, PDF generation), you need patterns that tolerate network interruptions and guarantee exactly-once outcomes.
Pattern 1: Idempotency keys – Make every critical POST safe to retry
An idempotent request returns the same result—without side effects—no matter how many times it is received. The usual technique is to add a unique Idempotency-Key header generated on the client side (UUIDv4, 128 bits of entropy is plenty). The server stores that key with a canonical response and re-serves the cached result if it sees the key again.
Typical eVisa touchpoints that must be idempotent:
POST /applications– create a new visa application recordPOST /payments– charge the traveler’s cardPOST /documents/:id/upload– upload a passport scan
Practical example
POST /applications HTTP/1.1
Idempotency-Key: 550e8400-e29b-41d4-a716-446655440000
Content-Type: application/json
{
"journey_id": "ABC123",
"traveler": { ... },
"visa_type": "single-entry"
}
If the OTA’s frontend times out after 10 seconds, the backend can safely retry the call—with the same key. The SimpleVisa API (and many payment gateways like Stripe) will recognise the duplicate and return the original 201 Created payload without billing twice.
Implementation tips
- Scope keys narrowly—one per resource-creating request—not per session.
- Store keys and responses in an indexed datastore for at least the natural life of a booking (often 48 hours).
- Return a deterministic error (409 or 422) if a second request tries to mutate a different payload under an existing key.
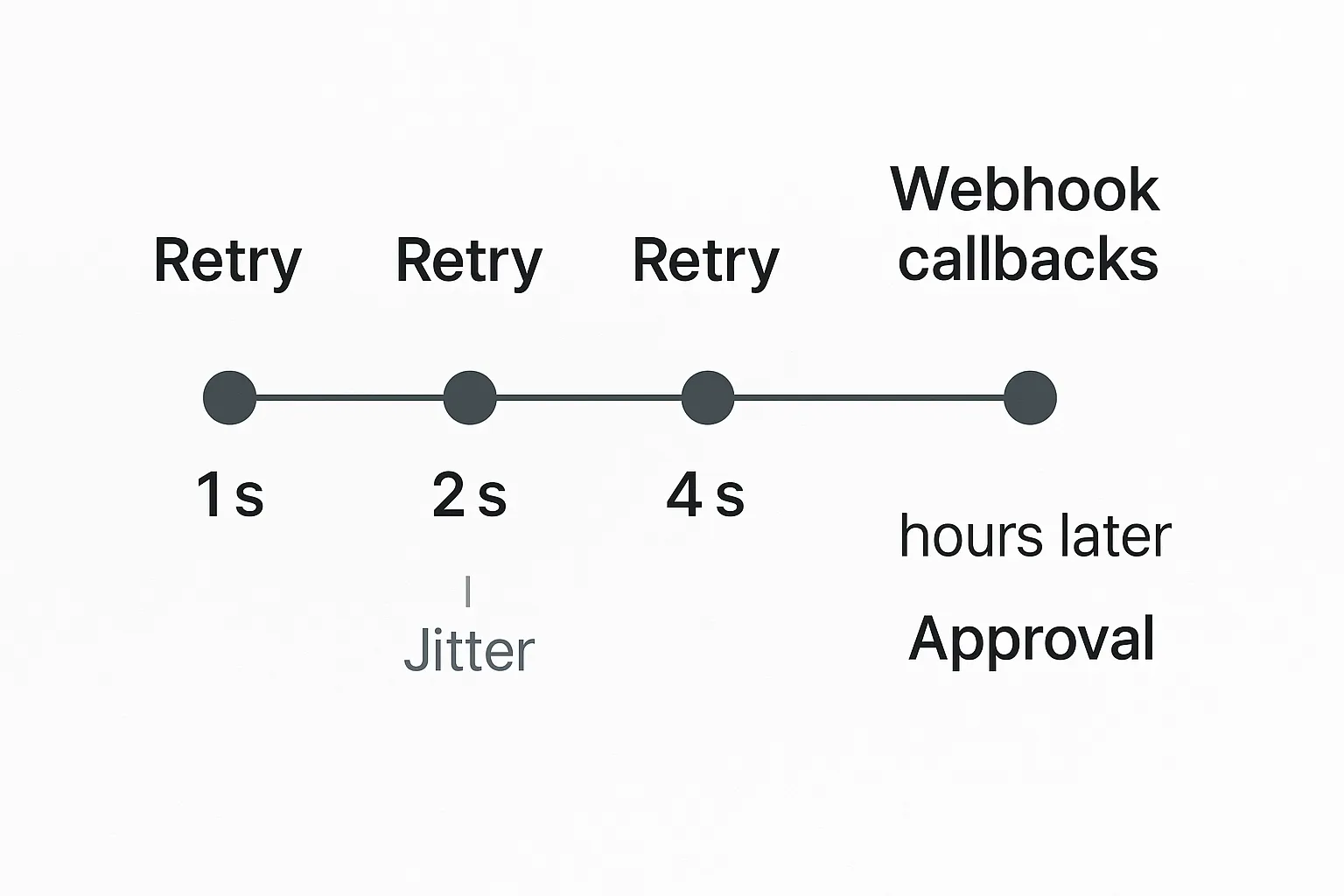
Pattern 2: Robust retries with exponential back-off and jitter
Even with idempotency in place, you still need a disciplined retry policy for transient failures (HTTP 429, 502, connection reset). Blindly looping every second will hammer rate limits and worsen outages.
| Error class | First retry delay | Max attempts | Notes |
|---|---|---|---|
| 429 Too Many Requests | Read Retry-After header or start at 2 s |
5 | Use token bucket maths to avoid spikes |
| 5xx (502, 503, 504) | 1 s, 2 s, 4 s, 8 s (+ random 0-0.5 s) | 4 | Exponential back-off with full jitter |
| Network timeout | Same as 5xx | 4 | Timeouts should be < server timeout to avoid double work |
For long-running eVisa steps (government processing can take minutes to days), polling is wasteful. This is where webhooks shine.
Pattern 3: Webhooks – Push status, don’t poll it
A webhook is an HTTP POST that the provider sends to your server when a state change occurs: application accepted, photo rejected, visa ready for download, etc.
Design principles
- Signed payloads – Verify
X-Signatureusing a shared secret (see Developer Q&A: Best Practices for Authenticating Against the SimpleVisa API). - At-least-once delivery – Providers usually retry webhooks (e.g., 5 times over 8 hours). Your handler must be idempotent—again.
- Rapid ACK – Return HTTP 200 within, say, 5 seconds. Do heavy lifting (database updates, email) asynchronously.
Consumer pseudocode
@app.post('/webhooks/simplevisa')
def handle_webhook(request):
if not verify_signature(request):
abort(400)
event_id = request.json['event_id']
if is_duplicate(event_id):
return '', 200 # Already processed
enqueue_job(request.json) # push to message queue
record_event(event_id)
return '', 200
Common eVisa webhook events
application.createdapplication.pending-reviewapplication.needs-action(e.g., blurred passport scan)application.approved(includes PDF download link)application.refused
By listening for approved you can auto-inject the visa PDF into the passenger’s trip timeline or send a branded “Ready to Fly” email—zero polling, zero wasted compute.
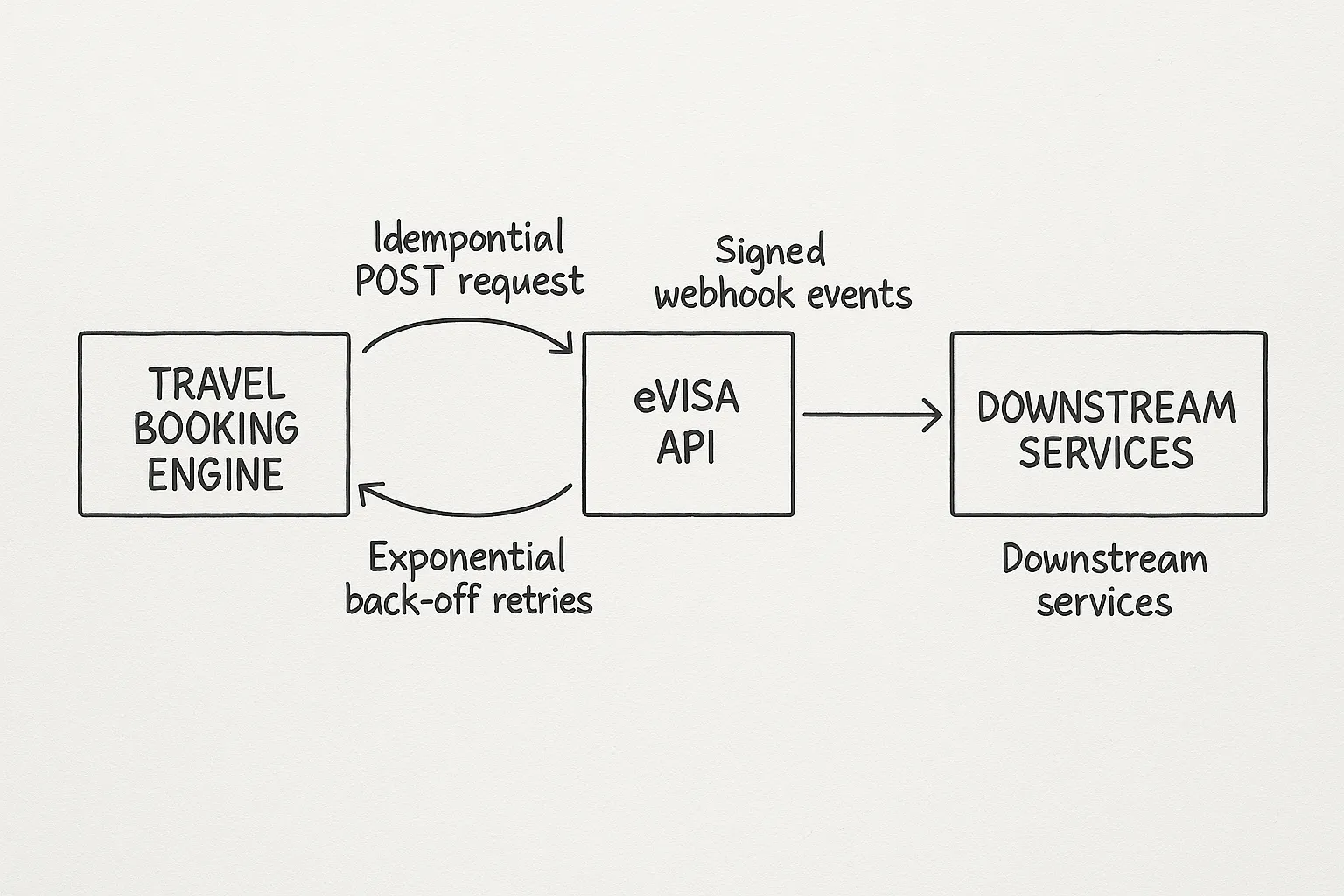
Putting it all together – A reference sequence
- Eligibility check – synchronous
GET /eligibility(cache for 24 h). - Application create –
POST /applicationswith an idempotency key. - Payment capture –
POST /paymentssame key or a new one scoped to payment. - Frontend redirects traveler to a hosted upload form (optional) while backend subscribes to webhooks.
- Webhook events drive status updates, triggering customer comms and CRM tasks.
- Visa PDF retrieval – when
application.approvedarrives, download once using thevisa_urlin the payload (also idempotent) and store securely.
Case snapshot – 30-day pilot with a mid-size OTA
After replacing manual polling with the pattern above, a Europe-based OTA integrating SimpleVisa saw:
- 42 percent reduction in API traffic (fewer status polls)
- Zero duplicate card charges across 18 000 transactions (idempotency keys enforced)
- 8.7 percent lift in visa attach rate thanks to faster, more reliable receipts that triggered timely upsell emails
Data on file with SimpleVisa Partnerships Team, July 2025.
Reliability checklist for your next sprint
- Generate UUIDv4
Idempotency-Keyfor every resource-creating call. - Store and cache idempotent responses for at least 48 h.
- Implement exponential back-off with full jitter; respect
Retry-After. - Treat 4xx (except 429) as non-retriable—surface to CX immediately.
- Verify webhook signatures and log the raw payload.
- De-duplicate events via
event_idbefore queuing work. - Keep handlers lightweight—ack within 5 s.
- Reconcile each booking nightly: API state ≈ local DB state.
Next steps
- Spin up a sandbox key and walk through the Step-by-Step Guide to Testing Sandbox eVisa Transactions.
- Review the full event catalogue in the Partner Portal and subscribe a webhook URL in staging.
- Explore where visa status can power upsell logic—see Future of Travel APIs: From Flights to Visas in a Single Call.
Ready to harden your eVisa flow? Book a 15-minute technical consultation with the SimpleVisa Solutions team and start shipping reliable, revenue-driving travel experiences today.